ePrescribing has become a core function in modern healthcare. It replaces paper scripts with faster and more accurate digital workflows that reduce transcription errors, minimize delays, and streamline pharmacy communication.
But speed and convenience aren’t enough. With every prescription transmitted electronically, sensitive patient data and authorization details are in motion. That creates a new kind of exposure, one that demands security controls as rigorous as the clinical decisions behind the prescription.
Especially in the case of controlled substances, where misuse or diversion carries legal and ethical consequences, the stakes are high. The system must verify that the prescriber is who they claim to be. It must protect the data in transit. And it must leave behind a trail that shows every action taken.
In this blog, we’ll explore the core security measures every ePrescribing system should have — from identity verification to encryption and audit logging.
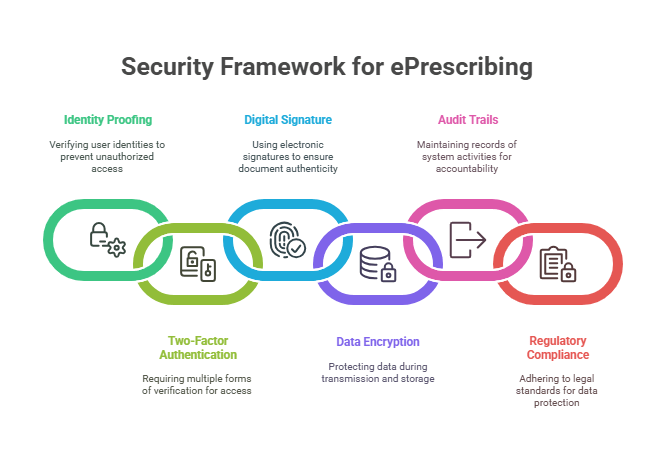
Identity Proofing and Two-Factor Authentication (2FA): Verifying Prescriber Identity
Before a provider can issue ePrescriptions—especially for controlled substances—they must first be verified as an authorized prescriber. This process starts with identity proofing, followed by two-factor authentication (2FA) each time a prescription is signed.
Identity Proofing
The DEA requires that prescribers undergo identity verification through an approved Credential Service Provider (CSP) or Registration Authority (RA). This step ensures the prescriber’s credentials and DEA number are legitimate before they’re granted access to any system capable of issuing controlled substances.
The verification process must meet the standards set by the National Institute of Standards and Technology (NIST) Special Publication 800-63-3, which outlines requirements for digital identity assurance, including multi-level identity vetting and secure credential issuance.
Once verified, the prescriber is issued credentials that are bound to their identity and linked to the prescribing system, typically via a token, mobile device app, or hardware-based solution.
Two-Factor Authentication (2FA)
Once credentialed, prescribers must authenticate themselves every time they issue a prescription for a controlled substance using two-factor authentication (2FA). This combines two elements:
- Something they know (like a password or PIN)
- Something they have (such as a cryptographic token or mobile authenticator app)
This approach protects against unauthorized access even if login credentials are compromised. The DEA mandates that the 2FA method must be approved under FIPS 140-2 cryptographic standards, ensuring the strength and security of the encryption technologies used.
Why It Matters
Together, identity proofing and 2FA establish a chain of trust. Only verified, credentialed prescribers can issue prescriptions, and each authorization event is logged, forming the first layer of defense in the ePrescribing security model.
According to the Office of the National Coordinator for Health IT, inadequate authentication and access controls remain one of the leading security gaps in EHR-integrated ePrescribing workflows, particularly in smaller or mid-size practices where administrative oversight is limited.
Digital Signatures: Ensuring Prescription Integrity
Once a prescription is written and the prescriber is authenticated, the system must ensure the prescription cannot be altered either in transit or after it reaches the pharmacy. This is where digital signatures play a critical role.
Unlike an image of a handwritten signature or a typed name, a digital signature is a cryptographic process that binds the prescriber’s identity to the content of the prescription. Any change made to the signed data, whether intentional or malicious, breaks that signature and invalidates the record.
How It Works
A digital signature is generated using the prescriber’s private key, which is part of a secure public key infrastructure (PKI). When a prescription is signed:
- A hash of the message content is created
- That hash is encrypted using the prescriber’s private key
- The result is attached to the prescription as a signature block
At the receiving end, the pharmacy system uses the public key to decrypt the signature and compare it to the prescription data. If they match, the prescription is confirmed as authentic and unchanged.
Standards and Certification
To comply with DEA EPCS requirements, ePrescribing systems must use cryptographic modules validated to FIPS 140-2 or higher — a federal standard for data security set by the National Institute of Standards and Technology (NIST). This ensures that the signature process isn’t just secure but also meets federally accepted benchmarks for tamper resistance.
In addition, systems must store the digital signature with the prescription record, allowing it to be verified later if needed for an audit, regulatory check, or legal inquiry.
Why It Matters
Digital signatures preserve trust in the prescribing system. Pharmacies can confirm that what they received is exactly what the prescriber intended. Health systems gain a verifiable chain of custody. And regulators have a reliable way to trace activity back to its source.
In an environment where controlled substances are involved, that level of assurance is foundational.
Encryption: Protecting Data in Transit and at Rest
ePrescribing systems handle a high volume of sensitive data from prescription details to patient identifiers, drug history, and provider credentials. To safeguard that information from interception or unauthorized access, encryption must be applied at multiple layers of the system.
Data in Transit
Any data transmitted between prescribers, pharmacies, and third-party intermediaries (like eRx networks) must be encrypted end-to-end. This means the information is converted into unreadable ciphertext before leaving the sender’s system and is only decrypted by the intended recipient.
Protocols like TLS 1.2 or higher are typically used to secure the transport layer. This prevents man-in-the-middle attacks, where a malicious actor could intercept or alter the prescription as it moves across networks.
DEA regulations for EPCS specifically require that all transmitted data, including digital signatures and authentication events, be secured using industry-standard encryption methods.
Data at Rest
Encryption doesn’t stop once the prescription is sent. Systems must also encrypt stored data, including prescription logs, patient profiles, and prescriber credentials, on local servers and cloud-based infrastructure.
This protects against data breaches resulting from device theft, unauthorized internal access, or server compromises. Storage encryption methods must align with NIST-recommended standards, such as AES-256, to ensure resilience against brute-force attacks.
Layered Security, Not a Single Feature
It’s worth noting that encryption works best when layered with access control, logging, and identity verification. But without encryption, even a well-audited system is vulnerable. All it takes is one exposed data stream or an unprotected storage volume for a breach to occur.
According to the 2024 DBIR, the healthcare sector experienced 1,378 security incidents, with 1,220 confirmed data breaches. This accounts for approximately 89% of incidents resulting in confirmed breaches within the healthcare industry.
This high percentage depicts the importance of robust security measures in the healthcare sector, especially concerning ePrescribing systems that handle sensitive patient data.
Audit Trails: Monitoring and Accountability
Effective ePrescribing security goes beyond access control — it requires a reliable record of every action taken across the system. That’s the purpose of audit trials: to create a tamper-resistant record of every key action in the prescribing process.
What Should Be Logged?
Audit trails in ePrescribing systems must capture a range of events, including:
- User login and logout activity
- Prescription creation, modification, and cancellation
- Two-factor authentication attempts and outcomes
- Digital signing events
- Transmission status (queued, sent, received)
- Refill and renewal requests
- System access by administrative users
Each log entry should include:
- A timestamp
- The user ID or device ID
- The action performed
- The patient or prescription ID involved
These logs are essential for both internal audits and external compliance reviews. They also serve as a forensic tool if any irregular prescribing behavior is flagged.
Regulatory Expectations
The DEA’s EPCS Final Rule mandates that ePrescribing systems maintain detailed, tamper-evident logs that preserve the integrity of controlled substance workflows. These audit trails must be stored securely, with access limited to authorized personnel, and retained for a period defined by federal and state regulations, often a minimum of two years.
The HIPAA Security Rule also reinforces the need for system activity monitoring, requiring covered entities and business associates to implement audit controls that record and examine system activity related to ePHI.
Why It Matters
Audit trails close the loop on accountability. They offer visibility into the prescribing process without relying on trust alone. If a prescription is challenged, if credentials are misused, or if a breach is suspected, the audit log is the first place investigators look.
More importantly, well-structured audit trails act as a deterrent. When users know their actions are being logged — and that logs are regularly reviewed — the risk of intentional misuse drops significantly.
Compliance with Regulatory Standards: DEA, NIST, and HIPAA
Strong security is essential in ePrescribing, but regulatory alignment is what makes that security legally and operationally valid. Systems involved in prescription generation and transmission must meet overlapping requirements from the DEA, NIST, and HIPAA, each targeting different layers of the process.
DEA – Drug Enforcement Administration (EPCS Requirements)
The DEA governs the secure electronic transmission of controlled substance prescriptions under its Electronic Prescriptions for Controlled Substances (EPCS) rule. Key requirements include:
- Identity proofing through approved Credential Service Providers (CSPs)
- Two-factor authentication for prescriber login
- Digital signatures bound to prescription content
- System audit trails to log every prescribing event
Only systems that meet DEA criteria — and are functionally certified — may transmit prescriptions for Schedule II through V drugs.
NIST – National Institute of Standards and Technology
While NIST doesn’t enforce ePrescribing regulations directly, its publications form the technical foundation for secure system design. Two key documents often cited in EHR and eRx compliance contexts:
- NIST SP 800-63-3: Guidelines for digital identity verification and assurance levels, used to define acceptable identity proofing and authentication processes.
- FIPS 140-2: Federal encryption standard required for cryptographic modules used in digital signatures and secure data transmission.
Systems that align with these standards are more likely to meet audit scrutiny and pass certification reviews required by CMS or the ONC.
HIPAA – Health Insurance Portability and Accountability Act
HIPAA governs the privacy and security of protected health information (PHI). In ePrescribing, HIPAA’s impact is broad:
- Ensures that patient data is only accessed by authorized personnel
- Requires safeguards like encryption, access controls, and transmission security
- Mandates that covered entities maintain and monitor system logs (aligned with audit trail expectations)
Failure to comply with HIPAA not only risks regulatory penalties but can also erode trust among patients and partner organizations.
Why This Matters
Regulatory compliance is not a one-time checklist — it’s a continuous alignment between technical infrastructure, user behavior, and system governance. Each of these standards plays a distinct role, and full compliance requires addressing all of them in concert.
Building Trust Through Secure ePrescribing
Most of what makes ePrescribing work isn’t visible. Patients don’t see the multi-factor authentication, the digital signature, or the audit log behind every refill. But those layers are what make the system trustworthy.
Security in this context is about making sure the right things happen for the right reasons, with proof to back it up. That’s what providers, pharmacies, and regulators all rely on — and what patients deserve.
If your team is building or refining secure ePrescribing capabilities, we can help make sure every layer holds up — technically, operationally, and in audit.
Reach out to us at info@nalashaa.com.
Latest posts by Priti Prabha (see all)
- ONC HTI 1 Final Rule and Certified APIs: A Complete Guide - February 19, 2026