Healthcare claims data is growing fast—billions of rows, dozens of formats, and constant schema shifts. At the same time, CMS keeps tightening the rules while cyber threats hammer already strained infrastructure. Yet despite years of digital transformation talk, 60% of payers still say claims-processing delays sit at the heart of provider friction. The reason? Core data needed for clean, fast adjudication lives in disconnected systems, riddled with inconsistencies.
Integrating claims data should be table stakes by now. Instead, payers and providers face the same recurring blockers—fragmented tech stacks, dirty inputs, outdated processes, and rising risk. This blog breaks down the five toughest challenges throttling healthcare claims integration and shows exactly where to go on offense.
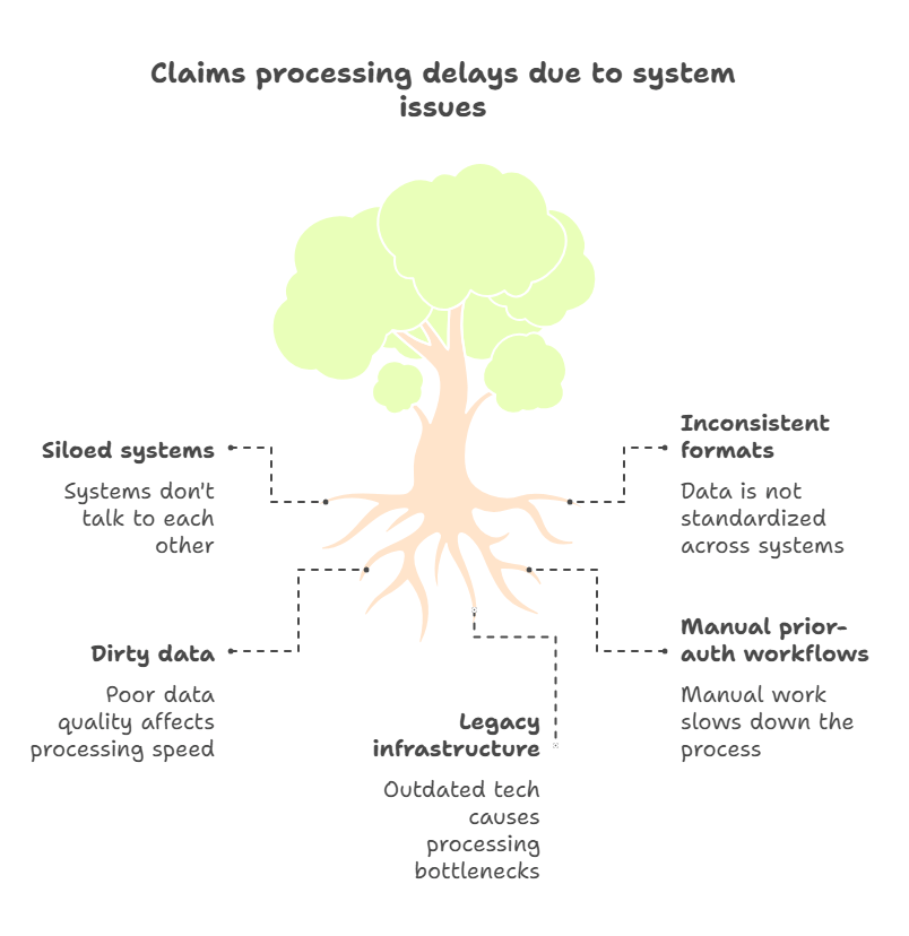
Challenge #1 — Fragmented Data Silos & Inconsistent Formats
The Problem
Fragmented data silos remain a core barrier. When workflows depend on extracting isolated facts instead of a holistic clinical context, interoperability collapses. An integrated diagnosis, prescription, or encounter may arrive stripped of meaning. That makes analytics inaccurate and decisions risky.
Industry data shows healthcare stakeholders keep facing a burden from redundant processes, billing errors from incompatible claim feeds, inaccessible patient records, and redundant testing, all traceable back to siloed data streams.
Regulatory pressure is mounting: 78% of countries surveyed now embed electronic data exchange standards in law, a global shift driving urgent modernization. Without standardized formats, integration costs spiral, onboarding slows, and provider satisfaction suffers.
Real-World Proof Points
- Approximately 70 % of healthcare executives cite operational inefficiencies tied to disconnected systems among the top challenges for 2025.
- In U.S. payer surveys, nearly half say lack of real-time visibility into claims transactions disrupts provider collaboration, a downstream effect of siloed formats and delays.
Fixes That Work
- Standardize with FHIR R4 & Bulk FHIR
Adopting FHIR R4 plus the Bulk FHIR spec provides a unified, REST‑style API toolkit and structured export mechanism. That standard removes one-off ETL scripts and reduces variability across data providers and claims formats.
- Leverage iPaaS or Low-Code Integration Tools
An integration hub or platform (iPaaS) acts as a normalization layer. It ingests diverse formats, flat files, HL7, proprietary APIs, and outputs consistent FHIR‑based payloads for downstream use. This approach speeds onboarding and reduces transformation overhead without heavy custom engineering.
- Implement Streaming Event Pipelines
Rather than waiting for nightly claim updates, streaming platforms (like Kafka or Pulsar) deliver claims-status events and adjudication metadata in sub-second intervals. That shift boosts real-time visibility and enables proactive action on emerging issues.
Challenge #2 — Poor Data & Weak Governance
The Problem
Poor-quality data and lax governance slow innovation and diminish trust in downstream analytics. In one recent survey, data quality gaps ranked among the top barriers to achieving analytics ROI in healthcare enterprises also report that around 80 % still face data-quality struggles that threaten AI accuracy and project success.
Proof Points
- The 2024 Healthcare Data Quality Report highlights pervasive data completeness and conformity issues across payers and providers.
- Level‑1 atomic data issues persist, thousands of variant codes for the same data point, inconsistently applied across sources.
Fixes That Deliver
- Establish a data-governance playbook with steward roles, shared reference catalogs, and automated validation rules applied at ingestion.
- Apply AI/ML techniques for cleansing: use NLP or pattern matching to auto-correct codes, dedupe records, and flag anomalies.
- Measure quality through KPIs like completeness, conformity, and timeliness. Report those metrics transparently to both IT and business teams for accountability.
Challenge #3 — Legacy Systems & Technical Debt
The Problem
Legacy IT causes integration friction and opens the door to security and compliance gaps. According to a 2021 HIMSS survey, roughly 73 % of providers still operate on unsupported operating systems with critical implications for interoperability and risk. Newer findings confirm that over 60 % of U.S. hospitals still rely on applications lacking cloud readiness, API support, or FHIR compatibility.
Proof Points
- A significant portion of critical hospital workloads still depends on unsupportable legacy OS, potentially missing security updates, as Windows 10 reaches end-of-life in October 2025.
- Legacy components block telehealth, analytics, and AI deployment by resisting integration and real-time data exchange.
Fixes That Work
- Strangler‑fig modernization: wrap legacy systems with modern FHIR microservices and incrementally decommission older modules.
- Use format‑agnostic adapters that bridge flat‑file or HL7 claim feeds into APIs or FHIR endpoints, easing transition and supporting backward compatibility.
- Bake modernization into capital planning: schedule incremental upgrades in every fiscal year to avoid accumulating technical debt and escalating risk.
Challenge #4 — Escalating Security & Privacy Risk
The Problem
Healthcare claims integrations involve sensitive data at every turn. Even short-lived missteps in authentication, encryption, or system isolation expose protected health information (PHI) and personally identifiable information (PII). These are not theoretical risks; they carry real consequences across financial, legal, and reputational dimensions (Reuters “new HIPAA Security Rule” coverage).
Ransomware attacks surged 264 % in 2024 alone, casting healthcare systems as prime targets due to their critical continuity needs and delayed modernization budgets.
Proof Points
- On February 21, 2024, Change Healthcare (processing nearly 40% of U.S. medical claims) experienced a ransomware breach via a remote-access portal lacking multi-factor authentication (MFA). Attackers exfiltrated six terabytes of data, compromising PHI for approximately 190 million individuals, the largest healthcare breach on record.
- The attackers demanded and received a ransom of $22 million in Bitcoin, yet data recovery failed, and recovery costs exceeded $2 billion for UnitedHealth Group, including direct payouts and provider reimbursements.
- The Department of Health and Human Services’ Office for Civil Rights is tightening enforcement: new HIPAA guidance includes mandatory MFA, encryption, routine security-risk analyses (SRAs), incident response plans, vendor oversight, and technical asset inventories.
- Broader sector trends confirm escalating exposure, major breaches now trigger multi-million-dollar litigation, long-haul class actions, and severe regulatory sanctions.
Fixes That Work
- Enforce zero‑trust integration practices: apply mutual TLS, least‑privilege service credentials, strong segmentation, and continuous posture scoring through every claims-access hop.
- Encrypt and tokenize PHI end‑to‑end: encrypt PHI in motion and at rest, tokenize identifiers like SSNs, and avoid passing raw HIPAA identifiers across systems.
- Cycle repeated SRAs and compliance drills: conduct deep security-risk analyses at least annually and after any key system change (per new HIPAA proposed rule requirements).
- Plan for disruption: design incident-response plans that link directly to claims workflow disruptions. Assume breach, practice resilience in claims pipelines, and ensure providers can continue adjudications even under partial system loss.
- Train teams and monitor vendors: deliver regular phishing and insider‑threat training, embed vendor oversight requirements into third-party contracts (including 24‑hour breach notifications), and monitor partner system hygiene under integrated claims flows.
Challenge #5 — Regulatory & Prior‑Authorization Pressure
The Problem
New CMS requirements under rule CMS‑0057‑F impose strict prior‑authorization deadlines, transparency mandates, and API obligations. Payers must respond to standard prior‑auth requests within seven calendar days and expedited requests within 72 hours beginning January 1, 2026. All impacted payers are also required to implement a Prior Authorization API by January 1, 2027, or rating years thereafter.
Many payers and providers remain unprepared: as of April 2025, 52% of providers and 43% of payers had not started work on their API implementations. Only 31% of payers reported being at least a quarter of the way through deployment.
Proof Points
- CMS mandates transparency into prior‑auth throughput and outcomes, with the first public reporting due March 31, 2026, reflecting calendar year 2025 data. Metrics include approval rates, denials, appeal outcomes, and average decision time.
- Payors must broaden Patient Access, Provider Access, and Payer‑to‑Payer APIs to surface prior‑authorization details (excluding drugs). These capabilities must be in production by January 1, 2027.
Fixes That Work
- Build FHIR‑based Prior Authorization APIs early: support lookup of requirements, decision status, and denial reasons—all mapped to standardized code sets. Use these APIs across workflow automation, EHR order sets, and provider portals for reuse and scale.
- Redesign prior‑auth workflows: eliminate manual faxes or phone calls. Enable providers to create end-to-end submissions, e‑decisions, and automated appeals. Align the key steps to APIs to shorten cycle time and reduce friction for providers.
- Publish and monitor PA metrics internally and externally: track time‑to‑decision, approval/denial rates, and extended-review cases. Share results publicly as required and use them proactively to benchmark and optimize operations.
- Embed compliance into governance: assign roles for monitoring CMS deadlines and reporting; test readiness well before 2026 and 2027 milestones. Include prior-auth modernization in fiscal planning cycles to spread implementation costs and avoid delays.
Quick-Hit Reference Architecture
Claims data integration succeeds when the architecture stays modular, event-aware, and API-first. Below is a streamlined reference stack designed for real-time claims status, prior-auth decisioning, and secure data sharing.
Source Systems
- EHRs and Provider Billing Systems: Originate claims, prior-auth requests, and encounter data.
- Core Admin Platforms: House eligibility, benefits, adjudication rules, and payment logic.
- Clearinghouses: Sit between providers and payers, normalizing 837/835 transactions and pushing acknowledgments.
- External Vendors: Risk adjustment, population health, or pharmacy data flows.
Integration Spine
- Event Bus: Kafka, Pulsar, or AWS Event Bridge streams status events, denials, and approvals in real time.
- FHIR APIs: Real-time transactions use R4/US Core endpoints; large-scale transfers handled via Bulk FHIR exports.
- Adapters: Flat-file or HL7 sources are normalized into FHIR via iPaaS or format bridges.
Data Services
- Data Quality Engine: Applies validation rules, transformation logic, and code standardization at ingest.
- Master Data Management (MDM): Resolves member identity across systems, links records, and deduplicates.
- Lineage & Observability: Tracks every transformation; logs latency, completeness, and downstream impact.
Security
- Zero-Trust Gateway: Enforces mutual TLS, rate limits, and per-client scopes for every integration.
- Data Loss Prevention (DLP): Prevents leakage of PHI in unstructured text or metadata.
- SIEM Feed: Streams access and anomaly data to enterprise security monitors and compliance dashboards.
Experience Layer
- Provider Portal: Surfaces prior-auth status, denial reasons, and remittance summaries.
- Member App: Displays claim history, explanation of benefits (EOB), and out-of-pocket tracking.
- Analytics Sandbox: Enables actuaries, data scientists, and compliance officers to run models and spot anomalies using fully de-identified, lineage-tracked data.
Readiness Checklist
Use this checklist to validate where your organization stands on claims integration readiness. Each question highlights a core requirement tied to operational scale, regulatory mandates, or technical resilience.
Claims Data Interoperability
- Can every upstream and downstream system push or pull FHIR R4 resources?
- Are Bulk FHIR exports supported for high-volume data exchange?
- Is there a consistent strategy for normalizing flat files, HL7, and APIs into FHIR?
Data Quality
- Are quality rules enforced at the point of data ingestion—before a claim hits adjudication?
- Do dashboards track completeness, conformity, and timeliness KPIs across all claim sources?
- Is there an assigned data steward or owner for claims data integrity?
Anomaly Detection
- What is the mean time to detect an anomalous claim or workflow failure today?
- Are real-time alerts and dashboards wired into claims-processing pipelines?
- Are historical claims data used to train models for predictive risk or fraud detection?
Prior Authorization & CMS Compliance
- Are Prior Auth and Claims Status APIs in development, testing, or live production?
- Are all CMS-0057-F requirements (decision times, denial reasons, reporting) mapped to your internal workflows?
- Which prior-auth metrics are published—and to which regulators, partners, or customers?
Technical Debt & Legacy Risks
- How many legacy components remain unwrapped by modern APIs or FHIR adapters?
- Is there a capital plan to retire outdated systems within 12–18 months?
- Do integration teams have visibility into technical debt blockers and upgrade timelines?
Conclusion
Clean, connected, and compliant claims data is the backbone of modern healthcare operations. Whether the goal is faster adjudication, real-time prior-auth, or tighter CMS alignment, integration challenges cannot be ignored. From siloed systems and dirty data to looming regulatory pressure, the risks are clear, but so are the opportunities.
Nalashaa helps payers and providers turn data chaos into clarity. Our Healthcare Data Analytics Services cover everything from FHIR API deployment and data quality automation to legacy modernization and AI-enabled insights. We build solutions that are fast to deploy, secure by design, and ready for tomorrow’s rules.
Let’s build smarter claims infrastructure together. Connect with us at info@nalashaa.com.
Latest posts by Priti Prabha (see all)
- ONC HTI 1 Final Rule and Certified APIs: A Complete Guide - February 19, 2026