The Health Insurance Portability and Accountability Act of 1996 was created to protect patient privacy and secure the handling of health data within the healthcare industry. This federal law outlines guidelines for how covered entities, such as healthcare providers and insurers, store and share protected health information. It also helps organizations by providing them with greater control over how their medical records are shared.
In this blog, we’ll examine HIPAA’s essential components, including privacy and security rules, breach notification requirements, and practical strategies to maintain compliance. We will also discuss the legal and ethical responsibilities healthcare professionals hold when it comes to safeguarding patient information.
Who Must Comply with HIPAA
HIPAA rule applies to certain organizations and individuals for better handling of PHI. These covered entities include:
- Health Plans such as HMOs, Medicare/Medicaid, and employer-sponsored health insurance.
- Health Care Providers that transmit health information electronically, including hospitals, clinics, and physicians.
- Health Care Clearinghouses that convert nonstandard data into standardized formats, often for billing and reimbursement purposes.
The law also covers business associates, meaning individuals or organizations that handle PHI on behalf of a covered entity. Examples include third-party billing services, data analytics firms, and IT vendors. Because these associates access sensitive medical data, they too must comply with HIPAA’s privacy and security requirements.
What Is Protected Health Information?
Protected Health Information is any data that can identify an individual and relate to their health status, the care they receive, or payment for that care. This can include obvious details like a patient’s name and birth date, but also extends to addresses, Social Security numbers, medical histories, and insurance details. The goal is to ensure that any information tying a person to their healthcare is handled with strict confidentiality.
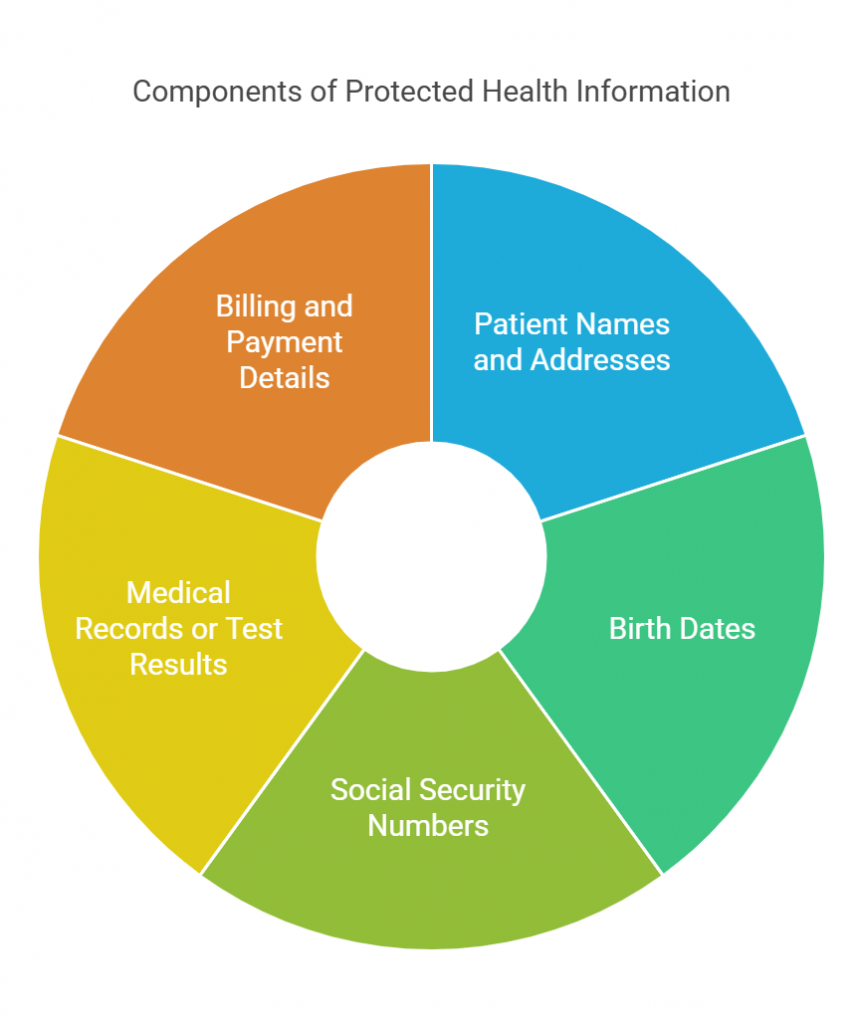
Whereas the data that has been stripped of all identifying details (like name, date of birth, and other unique markers) is no longer considered PHI. This de-identified information is used more freely, often for research or analytics, because it doesn’t reveal the identity of individual patients.
Permitted Uses and Disclosures of PHI
The law generally requires patients to authorize the use or disclosure of their protected health information. However, it also specifies situations where PHI can be shared without explicit permission:
- Treatment, Payment, and Health Care Operations (TPO)
This category covers everyday healthcare activities like diagnosing patients, billing insurance, and carrying out quality reviews. Since these tasks are part of standard care, no additional permission is necessary.
- Incidental Disclosures
These are minor disclosures that happen unintentionally as a result of permitted actions. For example, someone might overhear a patient’s name during a conversation or see part of a medical record left on a counter. While these disclosures are allowed, covered entities must put safeguards in place—such as speaking quietly or using private areas for discussions—to minimize risks.
- Additional Permitted Disclosures
PHI may also be shared for certain public health activities, law enforcement inquiries, or approved research initiatives. In these cases, only the minimum amount of information required should be disclosed, and the entity must follow HIPAA’s privacy and security guidelines.
- When Authorization Is Needed
For any use beyond these exceptions—such as marketing efforts or specialized research—HIPAA requires patients to give explicit written permission. This ensures individuals maintain control over how their personal health information is accessed and used.
Individual Rights Under HIPAA
One of the main elements of HIPAA is the set of rights it provides to patients, ensuring they remain informed and in control of their health information:
- Right to Access
Individuals can view and receive copies of their medical records, billing statements, and other related documents. While providers may charge a reasonable fee for reproducing records, they are required to respond to access requests promptly.
- Right to Amend
If a patient believes their records are incomplete or inaccurate, they can request updates. Although a provider might deny certain changes, they must explain why and give the patient an opportunity to file a written statement of disagreement.
- Right to an Accounting of Disclosures
Patients can obtain a list of specific instances where their protected health information was shared, with certain exceptions (such as disclosures related to treatment, payment, or healthcare operations).
- Notice of Privacy Practices (NPP)
All covered entities must provide a clear, written summary of how patient data is collected, used, and shared. This notice outlines the individual’s rights, as well as instructions for raising concerns or filing complaints.
The “Minimum Necessary” Standards for HIPAA Compliance
Protecting patient privacy is the “Minimum Necessary” standard in the HIPAA rule. This rule mandates that any person or organization handling PHI should limit access, use, or disclosure of that information to only what is needed to complete the specific task at hand. It minimizes how much data is shared to reduce the risk of exposing unnecessary personal details.
When It Applies
The minimum necessary requirement applies in most situations involving PHI, except for direct patient treatment, disclosures made to the individual, or instances mandated by law. Outside of these exceptions, covered entities and their workforce must ensure that only essential data is disclosed—no more than what is strictly needed for billing, quality checks, or other permissible operations.
Administrative Requirements for Compliance
HIPAA requires organizations to have structured processes in place to ensure compliance. These administrative measures help healthcare providers, insurers, and business associates define policies, assign responsibilities, and maintain records that demonstrate adherence to privacy and security standards.
Privacy Policies and Procedures
Every organization handling PHI must document policies detailing how data is stored, accessed, and shared. These policies must align with HIPAA’s privacy and security rules and be reviewed regularly to stay current with regulatory updates. A well-defined policy framework ensures that PHI is handled consistently and gives employees clear guidelines to follow.
Designation of a Privacy Official
Organizations must appoint a privacy official to oversee compliance efforts. This individual is the primary point of contact for privacy-related concerns, investigates potential HIPAA violations, and ensures that policies are implemented effectively. Their role includes coordinating with IT and legal teams to enforce security measures, address risks, and manage privacy training initiatives.
Workforce Training
Anyone who handles PHI must be trained in HIPAA’s privacy and security requirements. Employees should understand how to manage patient information securely, recognize potential risks, and know how to respond to unauthorized disclosures. Since privacy threats and regulations evolve, training should be an ongoing process, ensuring staff stays updated on compliance expectations.
Record Retention
HIPAA mandates that organizations maintain privacy policies, training records, and other compliance-related documentation for at least six years. This includes records of PHI disclosures, patient access requests, and any corrective actions taken in response to violations. Proper documentation not only supports compliance but also helps organizations respond effectively to audits or investigations.
Enforcement and Penalties
HIPAA compliance is monitored and enforced by the Office for Civil Rights (OCR) under the U.S. Department of Health and Human Services (HHS). The OCR investigates complaints, conducts audits, and takes action against violations to ensure that healthcare organizations and their business associates follow HIPAA regulations. Failure to comply can result in financial penalties, reputational damage, and, in severe cases, criminal charges.
Oversight and Investigations
The OCR has the authority to investigate any entity covered under HIPAA if a complaint is filed, a potential violation is identified, or a data breach occurs. Investigations may result from:
- Patient complaints about privacy violations.
- Reports of security breaches affecting PHI.
- Routine compliance audits.
- Self-reported breaches by covered entities or business associates.
If a violation is found, the OCR may require corrective action, issue financial penalties, or, in extreme cases, refer the matter to the Department of Justice for criminal prosecution.
Consequences for Noncompliance
HIPAA violations are classified into different tiers based on the severity of the offense and whether the violation was due to negligence or willful disregard of the law.
- Tier 1: Unintentional violations where the entity was unaware of the breach and could not have reasonably avoided it. Fines range from $100 to $50,000 per violation, with a maximum annual penalty of $25 million.
- Tier 2: Violations due to reasonable cause but not willful neglect. Fines range from $1,000 to $50,000 per violation, with an annual cap of $100,000.
- Tier 3: Violations due to willful neglect that were corrected within the required time frame. Fines range from $10,000 to $50,000 per violation, with an annual cap of $250,000.
- Tier 4: Violations due to willful neglect that were not corrected. The penalty is $50,000 per violation, with an annual cap of $1.5 million.
In addition to civil penalties, criminal charges can be imposed in severe cases, particularly where PHI is used for financial gain, fraud, or malicious intent. Criminal penalties may include fines ranging from $50,000 to $250,000 and imprisonment of up to 10 years.
Real-World Impact: Enforcement Actions and Data Breaches
Over the years, many healthcare organizations have faced penalties for HIPAA violations. Some notable enforcement actions include:
- Anthem Inc. (2018): The company was fined $16 million following a data breach that exposed nearly 79 million patient records due to cybersecurity failures.
- MD Anderson Cancer Center (2018): The organization was penalized $4.3 million after unencrypted devices containing PHI were lost, violating HIPAA’s security requirements.
- Aetna (2020): A settlement of $1 million was reached after PHI was disclosed improperly through mailing envelopes with visible patient information.
These cases highlight the financial and reputational risks associated with HIPAA violations. Organizations that fail to implement proper safeguards, employee training, and security measures may face severe consequences.
Tips and Best Practices for HIPAA Compliance
Keeping patient information secure requires directly relates to the daily decisions organizations make when handling PHI. Small lapses can lead to serious breaches, making it important to regularly assess security measures and reinforce best practices.
Compliance Checklist
Organizations that handle PHI should regularly check whether:
- Privacy policies are updated and aligned with HIPAA regulations.
- A designated privacy officer oversees compliance efforts.
- Employees receive regular training on how to handle PHI securely.
- Access to PHI is restricted based on job roles.
- Data encryption and secure storage measures are in place.
- Internal audits are conducted to catch and fix compliance gaps.
- A clear plan exists for responding to security breaches.
Everyday Tips for Protecting PHI
Beyond policies, everyday actions help prevent unauthorized access and data breaches. Some key practices include:
- Keeping discussions about patient information private.
- Using strong passwords and multi-factor authentication for electronic records.
- Securing paper records in locked storage.
- Encrypting emails that contain sensitive health information.
- Keeping software and security systems updated to reduce vulnerabilities.
A proactive approach to compliance helps organizations avoid risks and keep patient trust intact.
conclusion
HIPAA is a well-known standard in healthcare, shaping how patient information is protected and shared. It establishes clear rules for covered entities, grants individuals control over their health data, and holds organizations accountable for compliance. It is a foundation for maintaining trust between patients and healthcare providers. A single breach or failure to follow proper protocols can have serious consequences, both legally and reputationally.
Compliance isn’t a one-time task—it requires continuous updates, staff training, and strong security measures. As healthcare technology evolves, organizations must stay ahead of new risks while ensuring their systems and processes align with HIPAA’s changing requirements.
At Nalashaa Healthcare Solutions, we provide healthcare regulations and compliance services tailored to the needs of healthcare organizations. From risk assessments to HIPAA-compliant system development, our team helps businesses strengthen their security posture while ensuring compliance with industry regulations. Reach out to learn how we can support your organization in safeguarding patient data.
FAQs
What is a HIPAA violation?
A HIPAA violation occurs when a covered entity or business associate fails to follow the regulations set by the Health Insurance Portability and Accountability Act. This includes unauthorized access to patient records, sharing personal health information without permission, improper disposal of medical records, or failing to implement proper security measures to protect electronic health data. A violation can also happen if a healthcare organization does not notify patients and regulatory authorities after a data breach that compromises protected health information.
What are the three main rules of HIPAA?
HIPAA has three essential rules that define how healthcare organizations must protect patient information. The Privacy Rule governs the use and disclosure of protected health information, ensuring that patients have control over their data. The Security Rule sets guidelines for securing electronic health records through administrative, technical, and physical safeguards. The Breach Notification Rule mandates that organizations notify affected individuals and the Department of Health and Human Services (HHS) in the event of a security breach involving PHI.
What information can be shared without violating HIPAA?
Certain types of information can be shared under HIPAA without violating privacy regulations. Healthcare providers can disclose patient information for treatment purposes, billing and payment processing, and healthcare operations such as quality improvement and risk management. PHI can also be shared when required by law, for public health reporting, and in certain emergency situations. If the information has been properly de-identified, meaning it no longer contains identifiable patient details, it is no longer subject to HIPAA restrictions.
Which type of insurance is not covered under HIPAA?
HIPAA applies to health insurers, but it does not cover other types of insurance that do not handle healthcare transactions. Life insurance, disability insurance, and workers’ compensation plans are not subject to HIPAA regulations since they do not process medical claims or provide healthcare services. These insurance providers are not considered covered entities and are not required to follow HIPAA’s privacy and security rules.
What kind of health information is not protected by HIPAA?
HIPAA only protects individually identifiable health information that is maintained by covered entities, such as healthcare providers, health plans, and business associates. If health data is collected by an entity that is not covered under HIPAA, such as an independent researcher, a mobile health app that is not connected to a healthcare provider, or an employer managing workplace wellness programs, the information is not protected under HIPAA’s Privacy Rule. Personal health details shared voluntarily on social media, fitness trackers, or online health forums also fall outside HIPAA’s scope.
What is considered a PHI breach?
A PHI breach occurs when protected health information is accessed, disclosed, or used in a way that violates HIPAA regulations and compromises patient privacy. This could be the result of a hacking incident, loss or theft of unencrypted medical records, an employee accessing patient files without authorization, or mistakenly sending PHI to the wrong recipient. Under HIPAA’s Breach Notification Rule, covered entities must notify affected individuals, report the incident to HHS, and in cases where more than 500 individuals are impacted, inform the media.
How long must HIPAA records be retained?
HIPAA requires that privacy-related documents, security policies, and training records be retained for at least six years. This includes HIPAA compliance policies, employee training logs, records of PHI disclosures, and documentation of any reported breaches. While HIPAA sets this standard for documentation retention, medical record retention periods vary by state law, with some requiring records to be kept for longer periods.
Can a patient sue for a HIPAA violation?
HIPAA does not grant individuals the right to sue for violations. However, if a patient’s health information is mishandled, they can file a complaint with the Office for Civil Rights (OCR) under HHS. If an investigation confirms a violation, the OCR may impose penalties on the responsible entity. In some cases, patients may be able to file a lawsuit under state privacy laws if their health information is disclosed or misused.
Are text messages and emails considered HIPAA-compliant?
Text messages and emails containing PHI must be encrypted and sent through secure platforms to be HIPAA-compliant. Standard text messaging and unencrypted emails do not meet HIPAA’s security requirements and can lead to a violation if they expose patient information to unauthorized parties. Healthcare providers must use secure messaging systems that offer encryption, access controls, and audit logs to ensure compliance.
Does HIPAA apply to telehealth and virtual consultations?
HIPAA applies to telehealth services just as it does to in-person healthcare. Providers offering virtual consultations must use HIPAA-compliant platforms that encrypt patient data and secure communications. While temporary flexibilities were introduced during public health emergencies, healthcare organizations are still required to protect patient information when using telehealth services.
What happens if a healthcare provider accidentally violates HIPAA?
Accidental HIPAA violations, such as sending a medical record to the wrong recipient or discussing PHI in an unsecured setting, must be evaluated based on their impact. If the violation poses a risk to patient privacy, it must be reported under the Breach Notification Rule. Organizations are also required to take corrective action, which may involve employee retraining, updating security measures, or strengthening policies to prevent similar incidents in the future.
Latest posts by Priti Prabha (see all)
- ONC HTI 1 Final Rule and Certified APIs: A Complete Guide - February 19, 2026