Why Your Patient App Fails When It Reaches the EHR
You’ve built a sleek patient app. It checks all the boxes: clean UI, FHIR-based access, and clear value to end users. But the moment it interacts with the EHR ecosystem, things start to fall apart. Integration stalls. Security reviews drag on. The app needs patient context, but there is no standard way to launch it inside a provider’s workflow. And worst of all, adoption never really takes off.
This is a common scenario. Not because the app is poorly designed, but because it lacks the one framework that connects it to the clinical environment it is intended for: SMART on FHIR.
Most teams plan for FHIR, thinking data access is the hard part. But while FHIR allows apps to read and write clinical data, SMART on FHIR governs how those apps launch, how they authenticate users, and how they operate within the security and workflow expectations of an EHR.
If you are building or scaling a patient-facing healthcare app, SMART on FHIR is your app’s foundation.
This article explains:
- What SMART on FHIR enables that plain FHIR does not
- Where development teams typically go wrong
- What technical and compliance considerations matter most
- A roadmap for building SMART-ready apps that scale across health systems
What SMART on FHIR Enables?
At first glance, FHIR seems like the only thing a healthcare app needs to access patient data. It provides structured resources, RESTful endpoints, and a growing ecosystem of vendor support. But in live environments, data access is only part of the equation. Without SMART on FHIR, your app has no way to authenticate users, understand patient context, or launch securely from inside an EHR or patient portal.
SMART on FHIR acts as the missing link between your app and the clinical systems it needs to function within. It standardizes three critical layers:
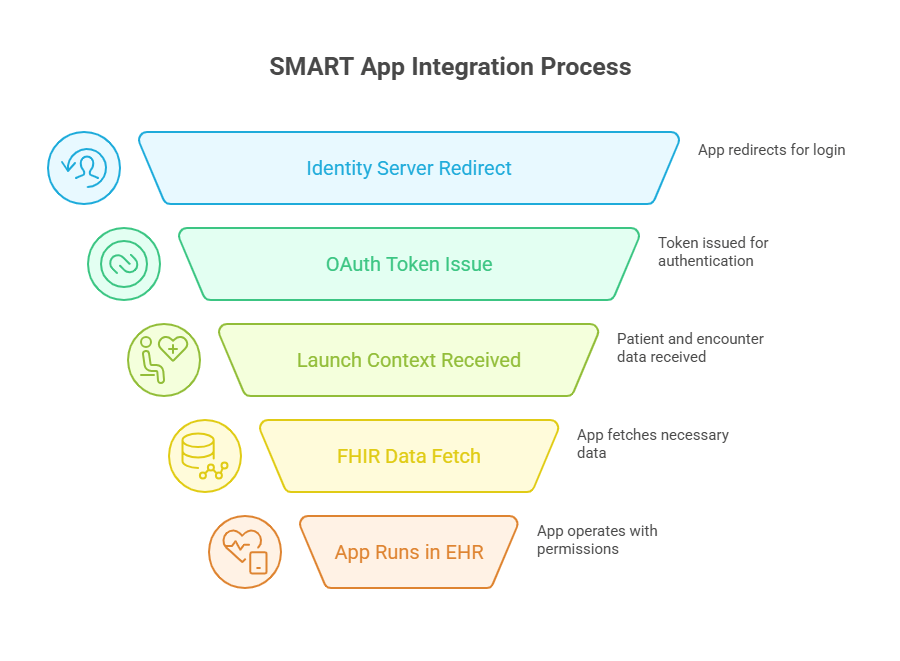
1. User Authentication
SMART uses OAuth 2.0 and OpenID Connect to authenticate users through the EHR’s identity provider. This allows apps to securely request access tokens tied to specific user roles, whether it’s a clinician, patient, or admin.
Without SMART, apps often rely on static tokens or inconsistent login flows, which lead to frequent session errors or access violations.
2. Contextual App Launch
SMART enables apps to launch directly within an EHR or portal and receive key parameters such as the current patient ID, encounter ID, or user identity. This reduces the need for users to reselect patients or re-enter information, creating a smoother experience.
For example, an app launched during a clinical visit can immediately know which patient is being seen and retrieve only the relevant data for that session.
3. Scoped Authorization
Using standardized scopes like patient/*.read or launch/patient, SMART defines exactly what data an app can access and under what circumstances. This ensures apps only retrieve what is necessary and align with both HIPAA and ONC’s data access guidelines.
Instead of requesting broad or undefined access, a SMART app communicates its needs clearly and predictably, improving both security posture and approval speed.
Together, these three functions allow healthcare apps to operate within the guardrails of enterprise systems, meet regulatory expectations, and provide seamless workflows for users.
Why FHIR Alone Falls Short
Many development teams assume that if their app can connect to a FHIR endpoint, they are ready for production. But FHIR, by itself, only handles the structure and transport of data. It does not manage who is accessing the data, how the app is launched, or what security measures are in place during that interaction.
Here is where FHIR begins to fall short in real-world deployments:
1. No Standard Login or Identity Flow
FHIR does not define how users authenticate. Without SMART, each EHR or provider system would require its own login setup, forcing developers to create custom workflows for every integration. This becomes nearly impossible to scale and adds a significant burden during security reviews.
SMART on FHIR solves this by using OAuth 2.0 and OpenID Connect to unify authentication. Apps can request tokens from the provider’s identity server and be granted access in a way that meets security and audit standards.
2. No Launch Context
A pure FHIR-based app might successfully retrieve data, but it does not know which patient the provider is currently seeing unless that information is manually passed in. That means users are forced to search for patients or select the same information twice—once in the EHR and again in the app.
SMART allows the EHR to pass that context automatically when launching the app. This includes identifiers for the patient, encounter, user, and more. The result is a seamless workflow where the app opens ready to use, without extra clicks or input.
3. Lack of Scoped Permissions
Without SMART, apps might request broad access or use static tokens that do not reflect the user’s role. This creates compliance risks and often triggers rejection from security teams during integration.
SMART enforces fine-grained scopes tied to user roles and session context. This helps developers build apps that request only what is needed, leading to faster security approvals and more trust from hosting organizations.
In short, FHIR is essential for accessing clinical data, but SMART on FHIR is what makes that access safe, controlled, and scalable inside actual healthcare systems.
Common Mistakes in SMART on FHIR Implementation
Even after teams commit to using SMART on FHIR, integration often fails during deployment. Not because of technical complexity alone, but due to incorrect assumptions, partial implementations, or lack of real-world testing. Below are the most common mistakes that prevent apps from running reliably inside EHR environments.
1. Partial or Incomplete OAuth2 Setup
Many teams implement only the basic token exchange, ignoring refresh tokens or failing to support short-lived access tokens. This leads to broken sessions, repeated logins, and security concerns during review.
What to do instead:
Follow the full OAuth 2.0 authorization code flow with support for refresh tokens. Handle token expiration gracefully, and store scopes in a way that aligns with user roles and session context.
2. Skipping Contextual Launch Parameters
Apps that do not support SMART launch parameters, such as launch, patient, or encounter, require users to manually search for information they have already selected in the EHR. This results in poor usability and lower adoption rates.
What to do instead:
Implement SMART’s contextual launch specification. Use the launch parameter to retrieve session-specific data from the EHR. Automatically focuses the app on the right patient and encounter without additional user input.
3. Assuming All FHIR Servers Behave the Same
Each EHR vendor implements SMART slightly differently. Scopes, endpoints, launch behavior, and metadata formats can vary. Hardcoding values or making assumptions based on sandbox environments leads to failures in production.
What to do instead:
Use SMART’s discovery endpoint at /.well-known/smart-configuration to dynamically adjust behavior based on the EHR hosting the app. Treat each server as a unique implementation and test accordingly.
4. Testing Only in Sandboxes
Public SMART sandboxes are useful for prototyping, but they do not represent the constraints of live deployments. Many production EHRs run apps in iframes, behind firewalls, or with strict security headers that break unprepared front ends.
What to do instead:
Test your app in multiple environments, including vendor-specific sandboxes and real-world QA environments when possible. Validate iframe behavior, token handling, and patient data loading in conditions that mimic actual clinical use.
5. Requesting Overly Broad Scopes
Requesting every possible scope during authentication might seem easier, but it often triggers red flags during a security review. Health systems want apps to access only what they need, no more.
What to do instead:
Use the minimum necessary scopes for your app’s core functions. If you need to read observations or medications, request only those resources. Align scopes with user roles and expected workflows to reduce review time and build trust.
Best Practices for Building SMART-Ready Healthcare Apps
Once you understand the role SMART on FHIR plays in enabling secure, contextual, and scalable app experiences, the next step is building for it correctly. The difference between a working prototype and a production-ready app lies in the details. These best practices will help ensure your app not only passes security reviews but also integrates cleanly into clinical workflows.
1. Follow the Full OAuth 2.0 Authorization Code Flow
Use the complete authorization code flow with short-lived access tokens and refresh token support. Store and manage tokens securely. Design your logic to handle session expiration and token renewal without interrupting the user experience.
2. Support Dynamic Configuration via Discovery Endpoints
Every SMART-compliant EHR provides a discovery endpoint at /.well-known/smart-configuration. Use this to retrieve the correct authorization and token URLs, supported scopes, and launch parameters. Avoid hardcoding endpoints or assuming uniform behavior across systems.
3. Handle Launch Context Smoothly
Expect and handle parameters like launch, patient, encounter, and practitioner at the start of your app session. These give you the context needed to load relevant data immediately. Failing to do so forces users to duplicate effort and breaks the embedded app experience.
4. Minimize Scope Requests
Limit your data access scopes to only what the app truly needs. This improves your chances of passing the security review, reduces risk exposure, and shows the host organization that you follow the principle of least privilege.
5. Test in Realistic Environments
Go beyond public SMART sandboxes. Use vendor-specific environments from Epic, Cerner, or other major platforms. Test inside iframes, within SSO contexts, and under variable network conditions. Real-world constraints often reveal issues that never show up in controlled environments.
6. Design for Embedded Use
Assume your app will be launched inside an iframe or mobile container. Handle scroll, resize, authentication refresh, and screen load states gracefully. Pay attention to page speed, error messaging, and visual stability, especially on older browsers or restricted networks.
These practices help ensure your SMART app is reliable, secure, and fully usable in the environments where it matters most—inside EHR workflows, patient portals, and clinical tools that demand consistency and trust.
Going Beyond Technical Readiness
Even with SMART on FHIR correctly implemented, many apps still stall during deployment. That’s because real-world success depends on more than compliant code. It also depends on how well the app fits into the workflows, risk models, and review processes of the healthcare organizations hosting it.
Technical readiness is only the first gate. To reach production and scale, you need to address three additional layers: organizational trust, integration friction, and approval workflows.
1. Organizational Trust Is Earned, Not Assumed
Enterprise health systems don’t automatically trust new apps, even if they are SMART-compliant. They want to know:
- How do you manage identity and consent
- What access does your app request, and why
- Whether you store any PHI outside the EHR environment
- How do you handle token expiration, logging, and audit trails
If these questions are not addressed up front, the review process becomes longer and more fragmented. Security and compliance teams want to see controls in place before they allow an app into their ecosystem.
What to do: Build a security and compliance package that explains your authentication model, data access scopes, consent handling, and logging practices. Include technical diagrams and documentation aligned to ONC and HIPAA requirements.
2. Integration Friction Slows Down Clinical Adoption
A SMART app might launch technically, but if it disrupts workflow, clinicians will not use it. That includes:
- Manual patient re-selection
- UI elements that do not match EHR styling
- Delays in data loading
- Interruptions due to token refresh or unexpected errors
Healthcare users expect the same level of polish and performance they experience in native EHR tools. Anything less creates resistance and disengagement.
What to do: Design for speed, clarity, and seamless launch. Minimize the number of clicks required to reach key functionality. Handle all launch context silently in the background so users can focus on the task, not the technology.
3. Approval Workflows Require Cross-Functional Buy-In
In most large health systems, apps go through a layered review process involving:
- Security and InfoSec teams
- Compliance and legal
- Clinical leadership or IT governance
- Sometimes, a vendor management or procurement team
Each group has its own concerns. If your team can’t clearly explain how the app meets identity, security, workflow, and regulatory expectations, the process slows or stalls entirely.
What to do: Prepare tailored documentation for each audience. Use SMART’s standard structures—such as scopes, tokens, and launch parameters—to demonstrate control and transparency. Avoid assuming the technical lead will also advocate for your app across departments.
Designing for Multi-EHR Scalability and QHIN Readiness
Healthcare app developers often validate their SMART on FHIR implementation against a single EHR or sandbox environment. While that might work for pilot testing, it does not prepare the app for scale. Every major EHR vendor—Epic, Cerner, MEDITECH, Athenahealth, and others—implements SMART slightly differently. Scopes vary. Launch behavior differs. Token endpoints might require custom handling.
What works in one environment can fail silently in another.
The next level of SMART readiness is multi-EHR scalability. That means your app should:
- Dynamically discover endpoints using the SMART metadata URL
- Handle different patient and encounter ID formats
- Adapt to iframe behavior, SSO sessions, and timeout rules across vendors
- Support varying combinations of launch context and access scope requirements
At the same time, participation in TEFCA and Qualified Health Information Networks (QHINs) is reshaping how patient data is exchanged across networks. While SMART on FHIR operates at the app level, QHIN connectivity impacts how that data is trusted, routed, and governed at a scale.
Your app may not connect directly to a QHIN, but it will increasingly operate within an ecosystem influenced by TEFCA policies, consent rules, and national exchange standards.
What to do:
- Plan for a modular architecture that can adapt across EHR implementations.
- Monitor QHIN adoption trends for your client base.
- Align your app’s identity, consent, and security flows with national-level exchange expectations.
Scalability is not just about supporting more users. It’s about surviving the complexity of real-world healthcare infrastructure.
Quantifying the Benefits of a SMART-Ready App
Investing in proper SMART on FHIR implementation is more than checking a compliance box. It creates measurable gains across performance, deployment, and trust. Below are outcomes we consistently see when teams move beyond surface-level FHIR integration.
1. Faster Go-Live Across Multiple Health Systems
Apps that follow SMART’s authentication and launch standards can be onboarded with fewer customizations. Security teams spend less time reviewing vague token logic or undefined scopes.
Result:
Up to 40 percent reduction in onboarding time when compared to apps with incomplete OAuth implementations.
2. Improved Clinical Adoption
With contextual launch and minimal user friction, SMART-enabled apps fit more naturally into clinical workflows. Users can open the app from within the EHR, with the correct patient context already loaded.
Result:
Clinician engagement increases, and workflow disruption decreases. Apps with embedded SMART flows report 2 to 3 times higher repeat usage than those requiring manual patient selection.
3. Reduced Support and Maintenance Costs
SMART’s dynamic discovery and scoped access reduce breakpoints caused by hardcoded endpoints or overbroad permissions. Fewer integration issues mean fewer tickets and less rework after deployment.
Result:
Organizations report a 30 to 50 percent drop in support effort post-launch when SMART is fully implemented and tested across environments.
4. Stronger Security and Compliance Posture
By using standardized scopes, short-lived tokens, and provider-managed identity, apps demonstrate alignment with HIPAA and ONC guidance without needing custom security models for each deployment.
Result:
Faster approval from security teams, reduced audit exposure, and higher trust from host organizations.
Conclusion
SMART on FHIR is the gateway to real interoperability — the kind that allows healthcare apps to operate securely, contextually, and at scale inside live clinical systems.
Building with SMART is a strategic choice. It aligns your app with EHR expectations, national data exchange mandates, and modern identity frameworks. It also prepares your product to operate within larger networks influenced by TEFCA, QHINs, and evolving data governance models.
If your organization is investing in healthcare interoperability solutions, SMART on FHIR should be central to your approach. From authentication to app launch and data access, it defines how scalable, secure integration is done today.
Have questions or need help with SMART on FHIR implementation? Connect with us at info@nalashaa.com to get started.